
SaaS providers send machine-generated emails to users (think: no-reply@acme.com), making email a powerful SaaS event log.
to Google Workspace or Microsoft 365 one time. That’s it.
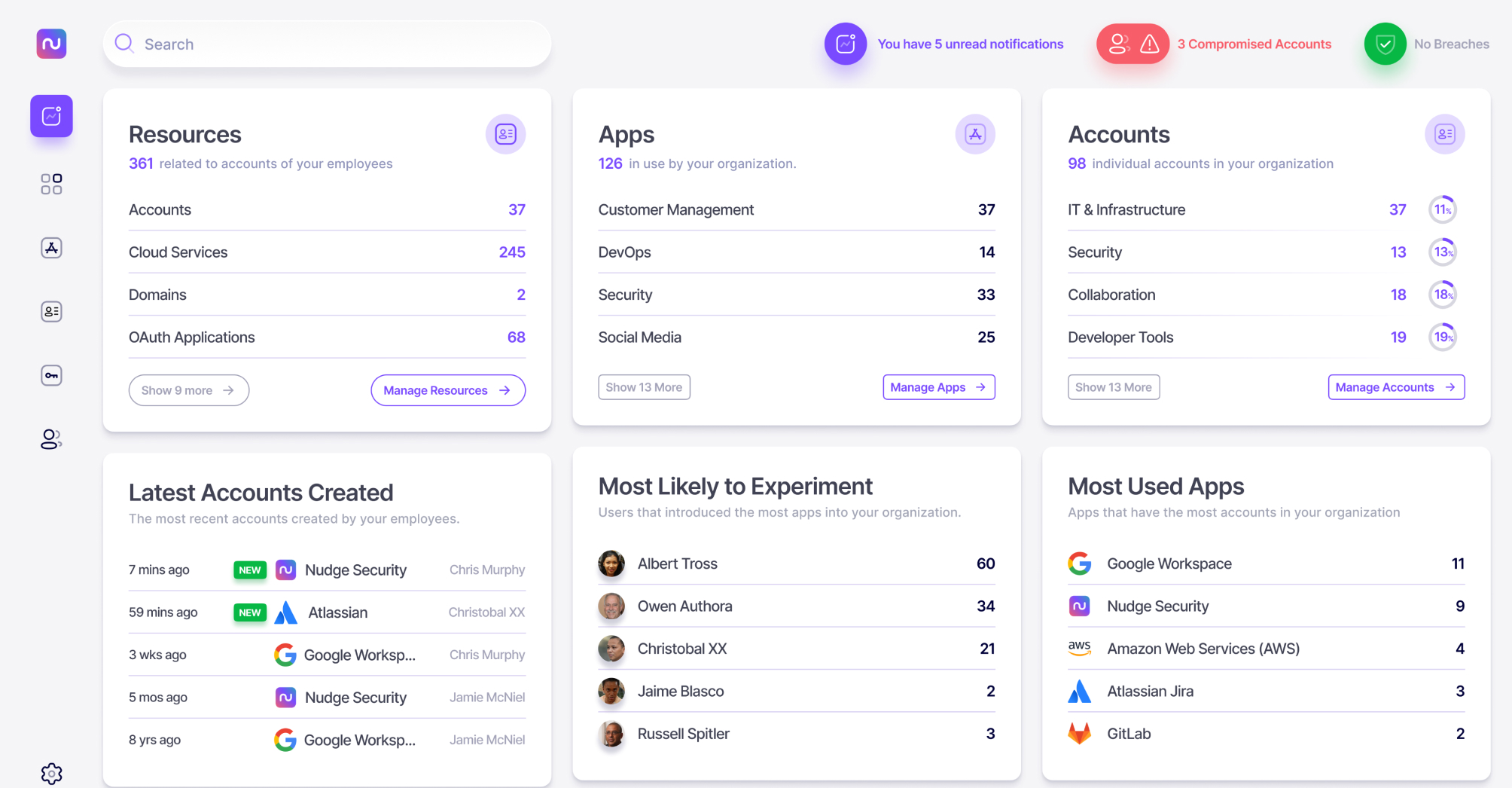
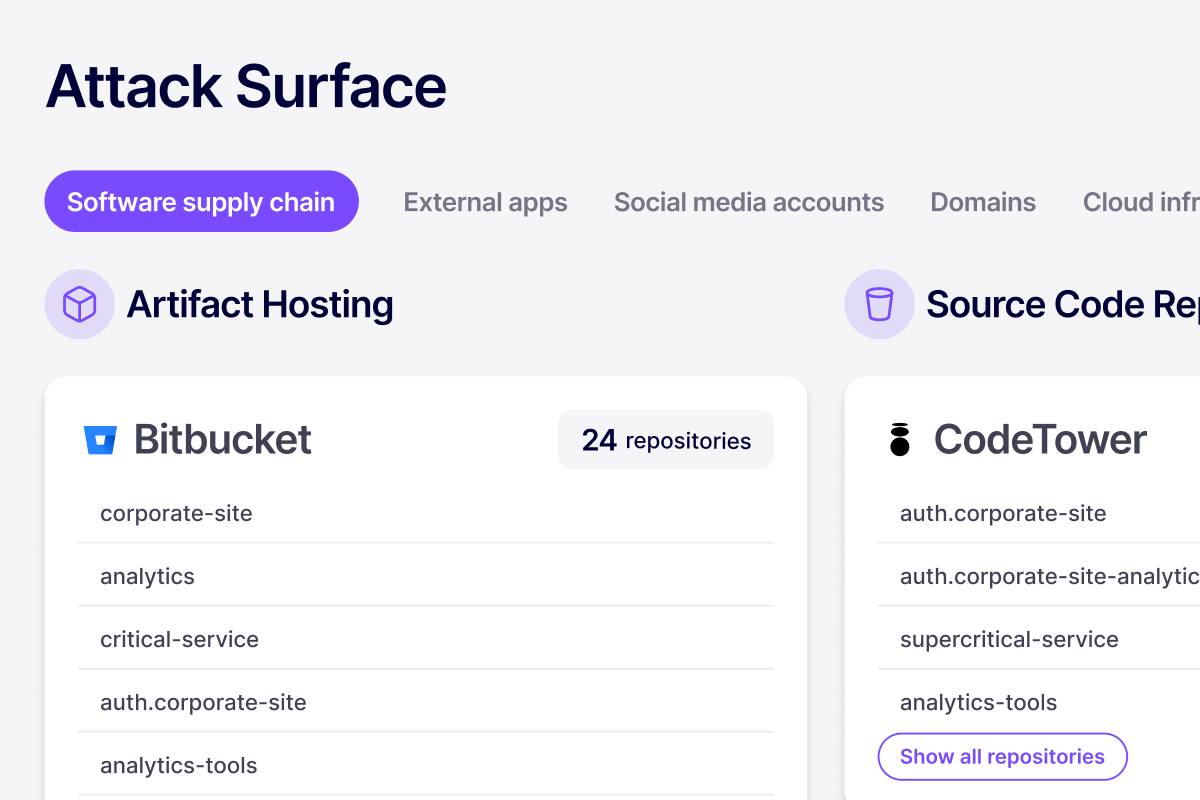
all cloud and SaaS accounts, historically and continuously.
providers’ risk postures, supply chains, and breach data in actionable dashboards.
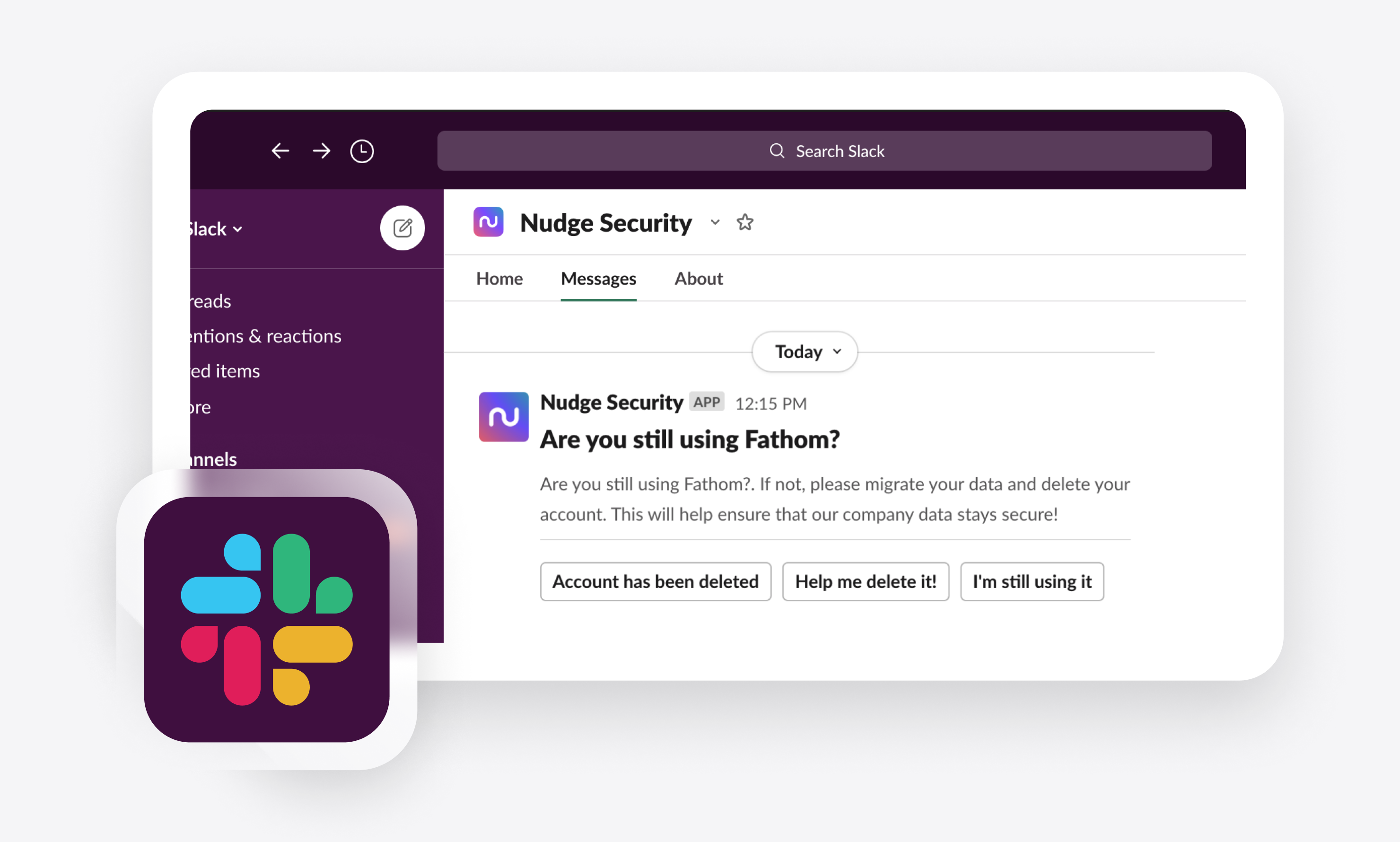
your employees toward better security behaviors with automated, real-time outreach.
common SaaS security tasks with playbooks that initiate time-saving workflows.
Curbing shadow IT is a manual, disruptive, and delayed forensics process (if done at all).
Employees are frustrated by archaic IT policies. They find workarounds or worse—new jobs.
Spreadsheets are used to track compliance scope, access reviews, SSO enrollment, and more.
Third-party vendor risk assessments are conducted infrequently with stale vendor data.
Employees retain access or leave orphaned accounts when exiting or changing roles.
SaaS assets are discovered and categorized as soon as they are created, anywhere, any device.
Embrace employee-led SaaS adoption without losing oversight or adding overhead.
SaaS security workflows run automatically. Dashboards make it easy to track progress and report.
SaaS vendor risk, supply chain, and breach data is gathered continuously and independently.
Employee offboarding is streamlined and secure, with automated workflows to transition accounts and owned resources.