Discover your organization’s unmanaged AWS accounts and automate workflows to enroll them in centralized governance.
In previous posts, we’ve talked about the dangers of rogue or unmonitored AWS accounts, and how much they can cost your organization. To recap:
Here, we’ll dig into the alternative: automatically identifying cloud accounts as soon as they’re created, so you can add them to your centralized governance process immediately and make sure they’re configured correctly.
Nudge Security gives you visibility of all of your organization’s cloud assets—including the unmonitored accounts your employees may have forgotten about—so you can avoid unnecessary costs and security risks. For Amazon AWS, you can even run a simple, automated playbook to discover existing AWS accounts, alert you to new ones as they’re created, and bring them into centralized governance. Any time an employee creates a new cloud account, you can also nudge them to use your organization’s preferred cloud services provider, justify their usage, or take security measures like enabling MFA.
Before we get into the step-by-step guidance, here’s a quick, interactive demo showing how to identify unmanaged AWS accounts using Nudge Security. If you want to see your own AWS accounts, you can also kick off a free trial and try it free for 14 days.
Nudge Security discovers all the cloud and SaaS assets associated with your organization, including accounts with major cloud service providers like Amazon AWS, Google Cloud Platform, and Microsoft Azure. Even if your organization doesn’t consider itself multi-cloud, you may be surprised by what you find!
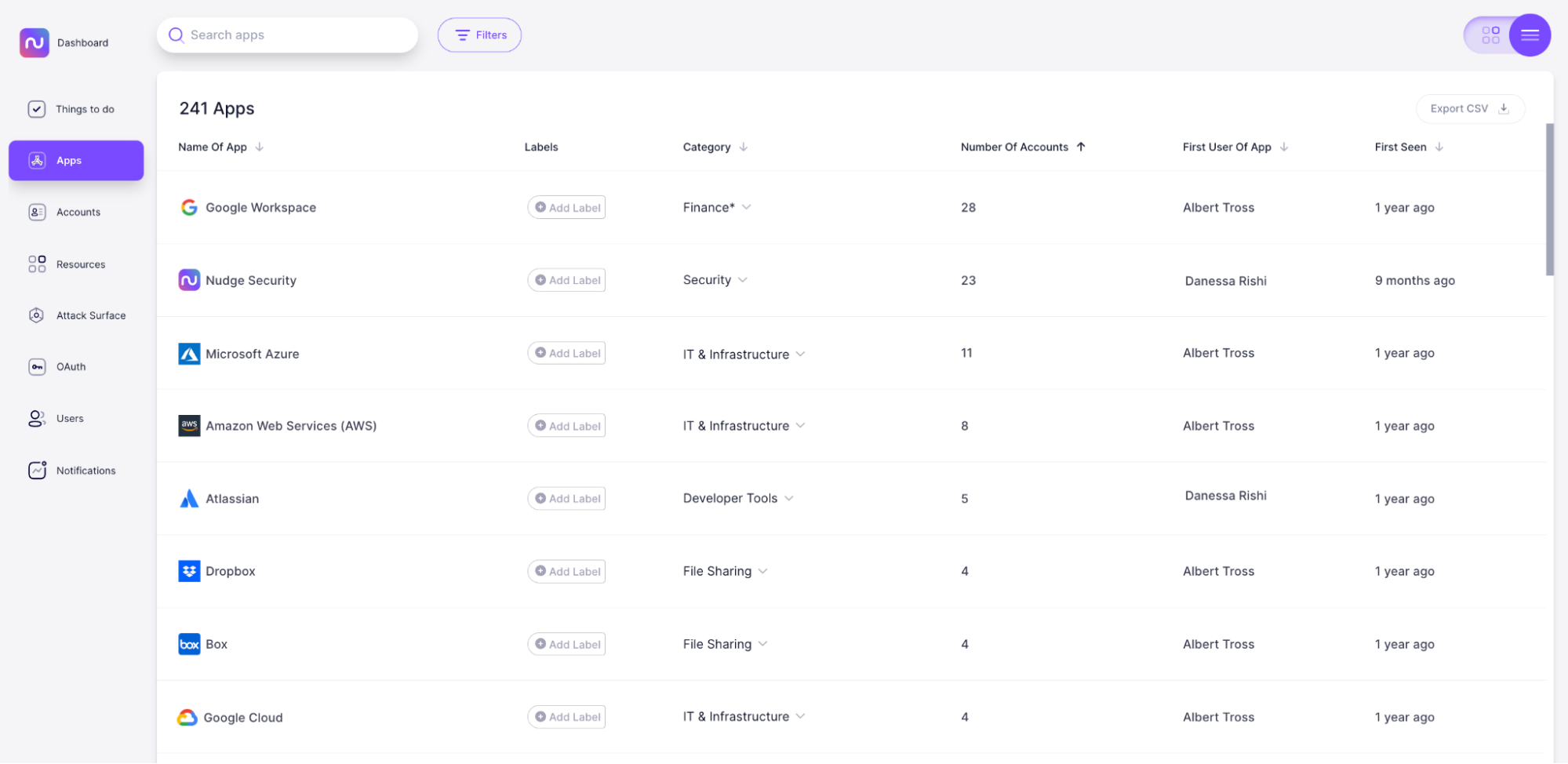
Nudge Security provides a dashboard showing your AWS Organizations and the accounts within them, as well as the unmanaged accounts that aren’t currently associated with an AWS Organization. You can search, filter, and export the data.
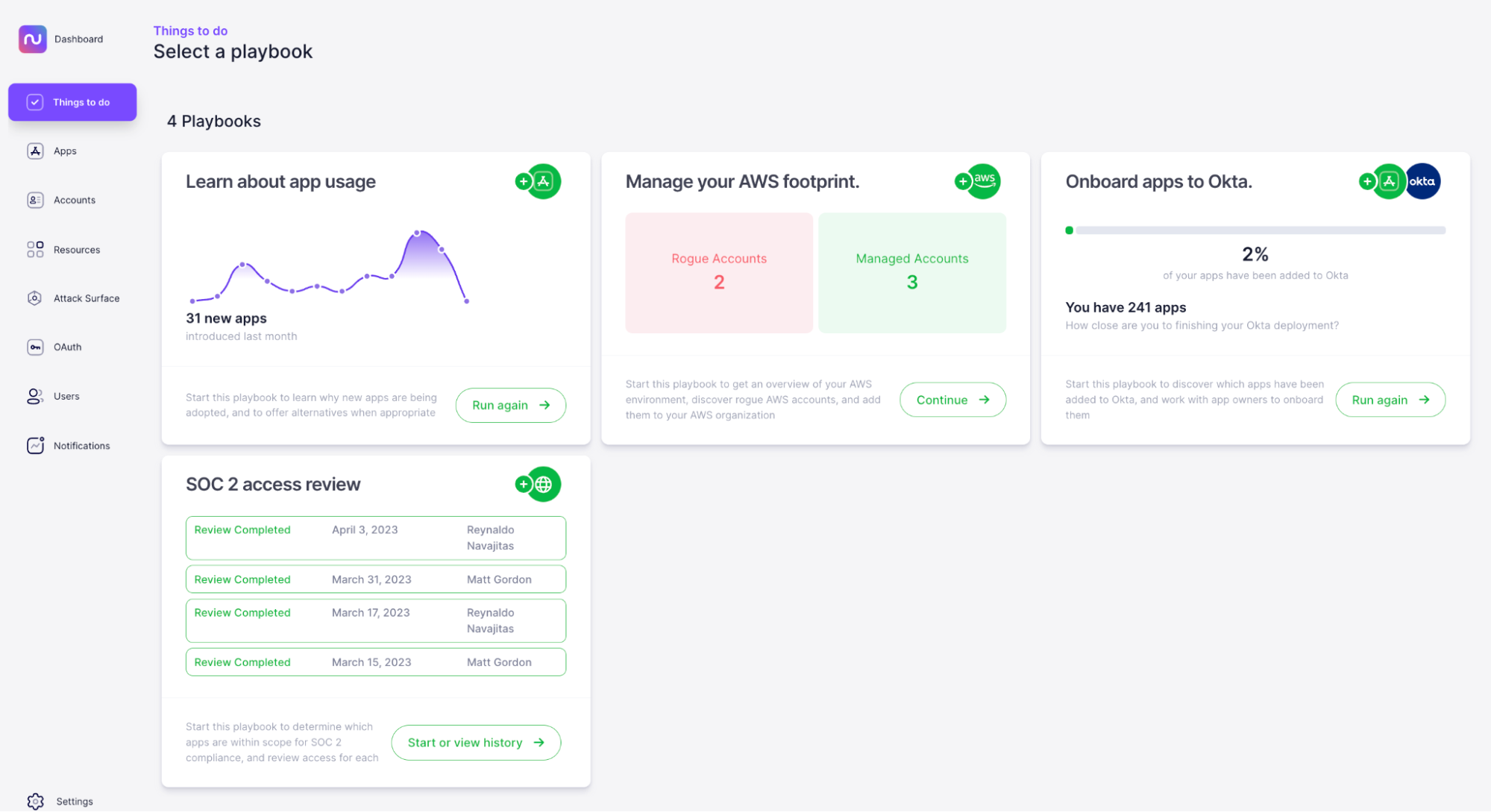
Take control of your AWS accounts with Nudge Security’s automated playbook that walks you, step-by-step, through discovering and managing your organization’s AWS footprint. You can see an at-a-glance count of your managed and unmanaged accounts at the beginning of the playbook.
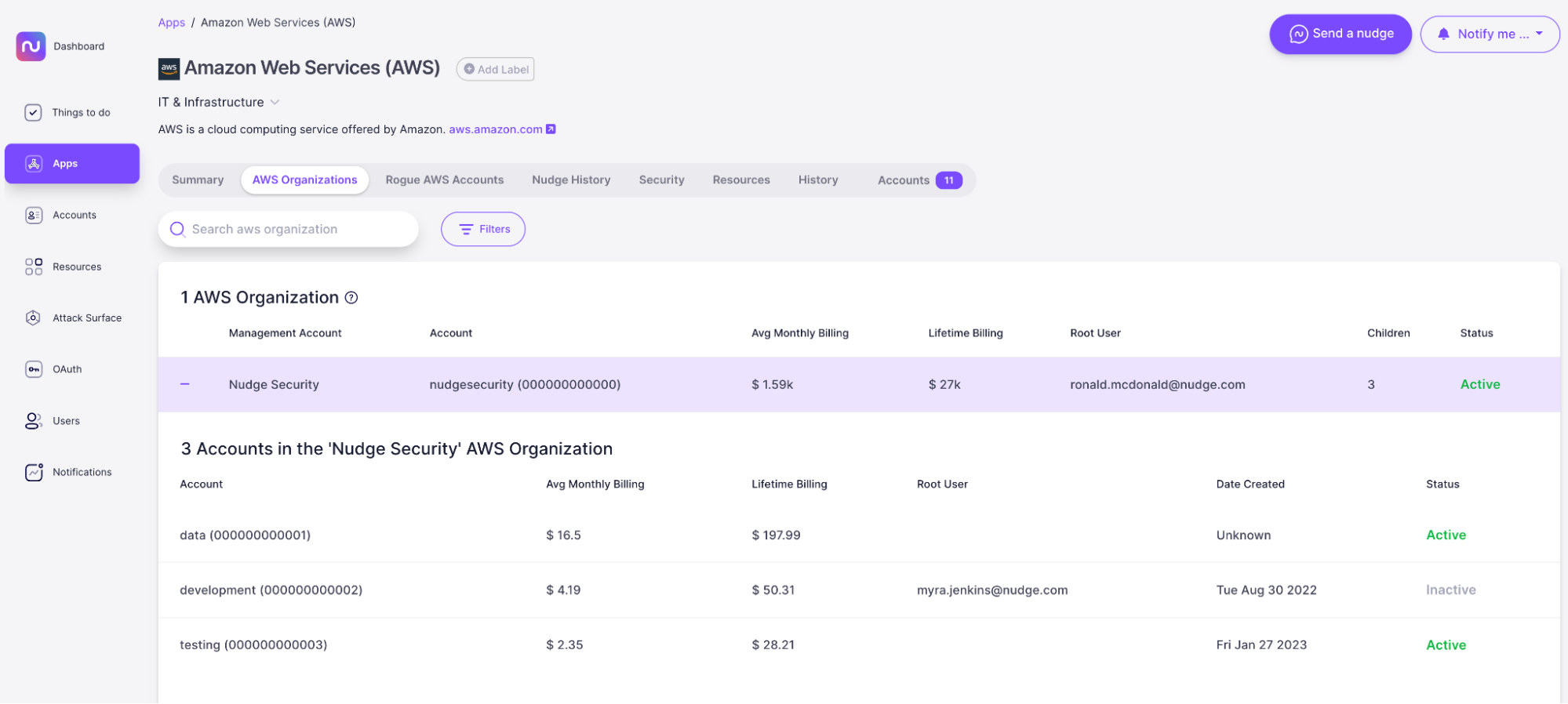
Nudge Security shows you all the AWS accounts that your developers have created, whether they remember doing so or not. This includes historical accounts that may have been abandoned over time, as well as accounts with owners who may have left your organization. For each account, we show you the AWS account number, the amount that has been billed, the date it was created, its activity status (active or inactive), and the name of the root user who created it.
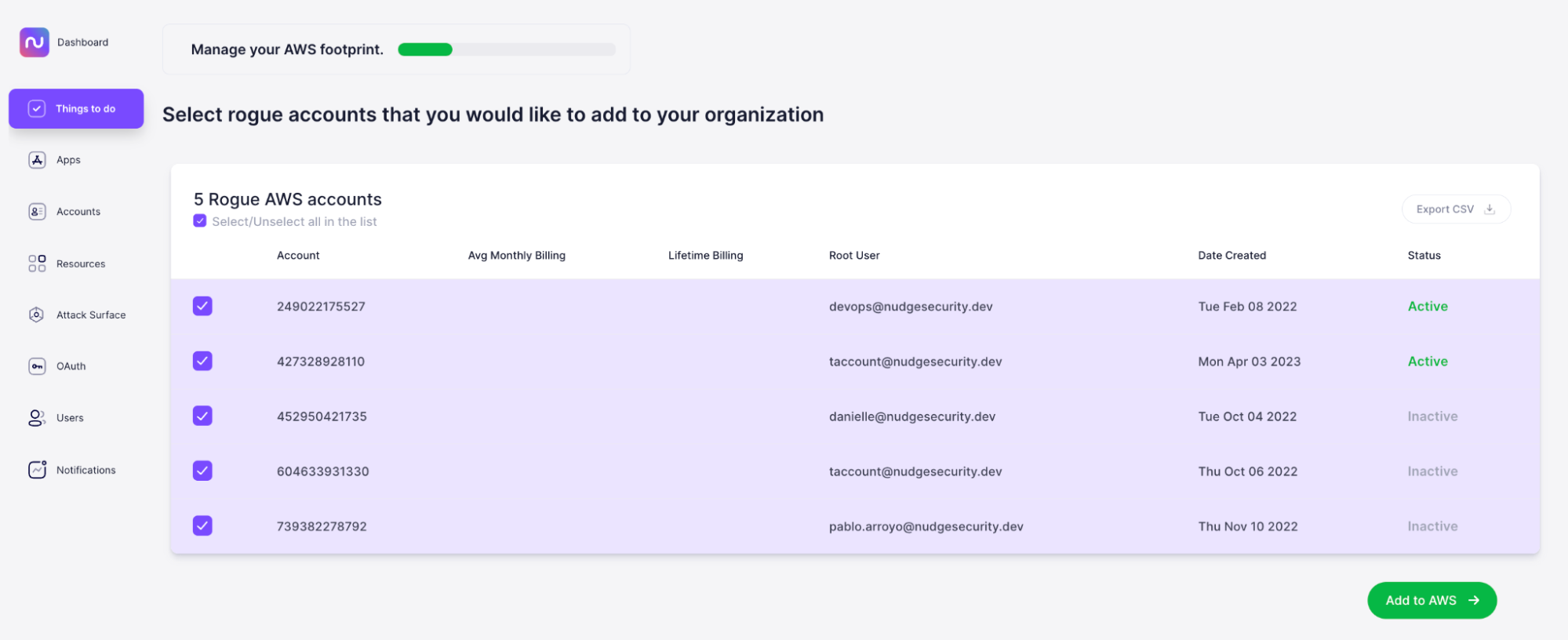
From here, you can invite unmonitored accounts to your AWS Organization, either via command line or by pasting each AWS account number into the invite field within your AWS account.
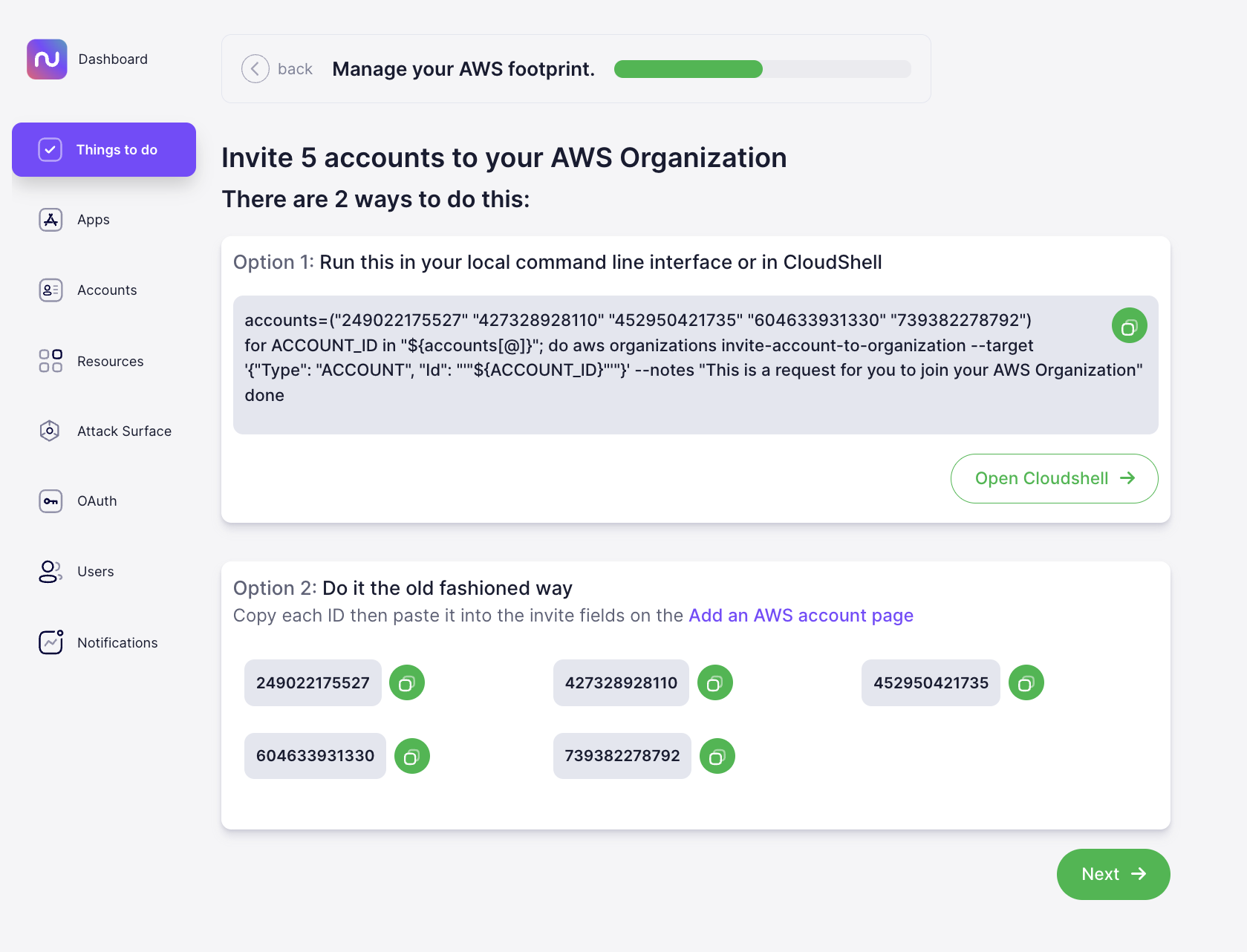
Ah, the old “trust, but verify.” As much as we’d love to trust each and every employee to remember to follow your organization’s centralized governance process, mistakes happen—and at complex organizations, acquisitions or distributed responsibilities for managing cloud services call for programmatic solutions rather than relying on individual employees.
Nudge Security enables you to set up automated alerts when your employees create new AWS accounts so you can make sure they’re configured correctly and centrally governed.
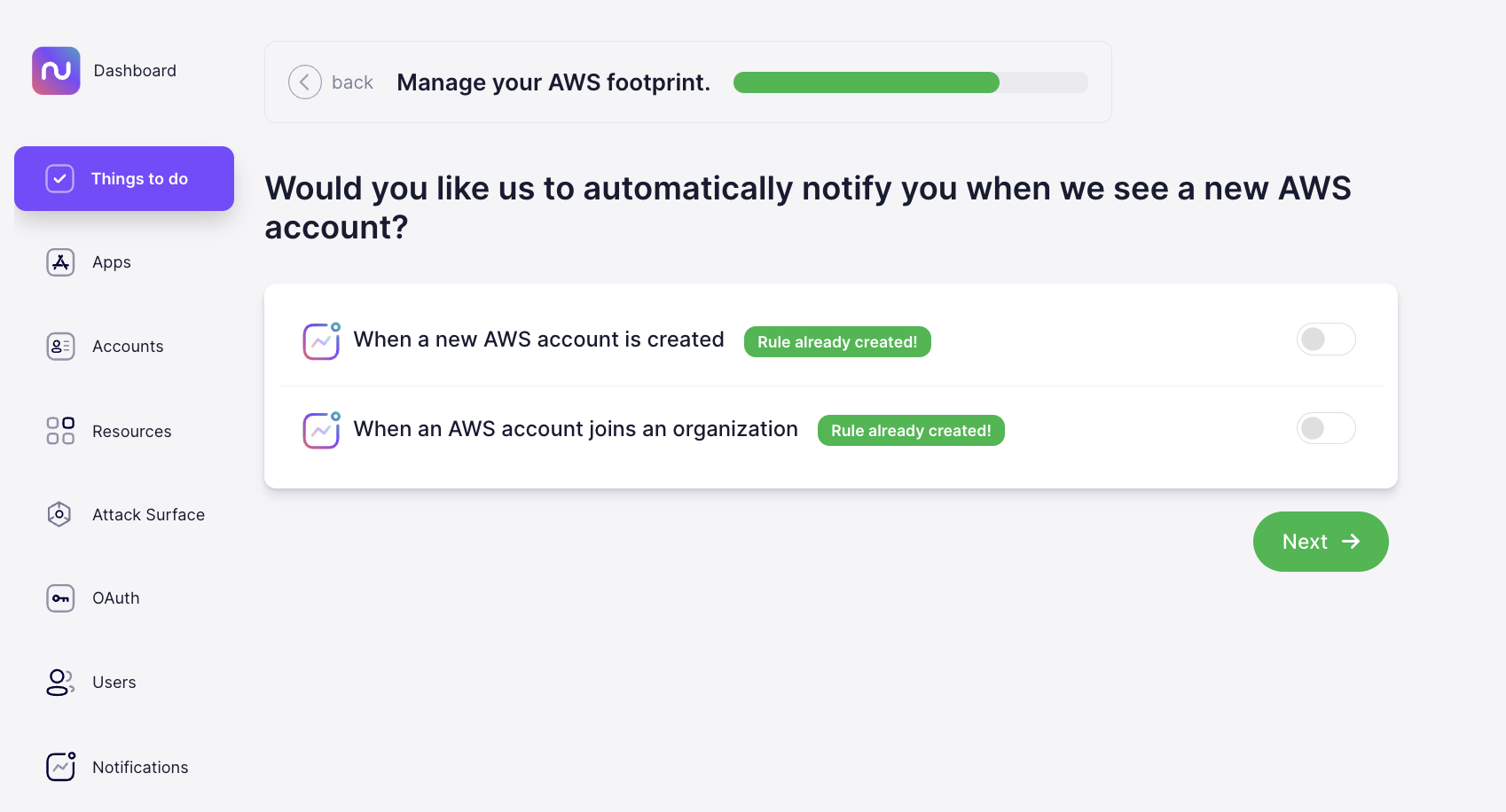
If your organization has an agreement in place with certain cloud providers, you might want to encourage employees to stick to your preferred vendors to take advantage of pre-purchased credits or favorable pricing. Nudge Security enables you to nudge employees automatically any time they create an account with a provider you’d prefer they avoid with a request to either explain why the account is necessary or switch to your preferred provider. You can also nudge employees to tell you whether they’re still using an account or encourage them to enable security measures such as MFA. With Nudge Security’s Slack integration, your employee can respond to nudges directly within Slack, and you’ll see their answers within the Nudge Security dashboard.
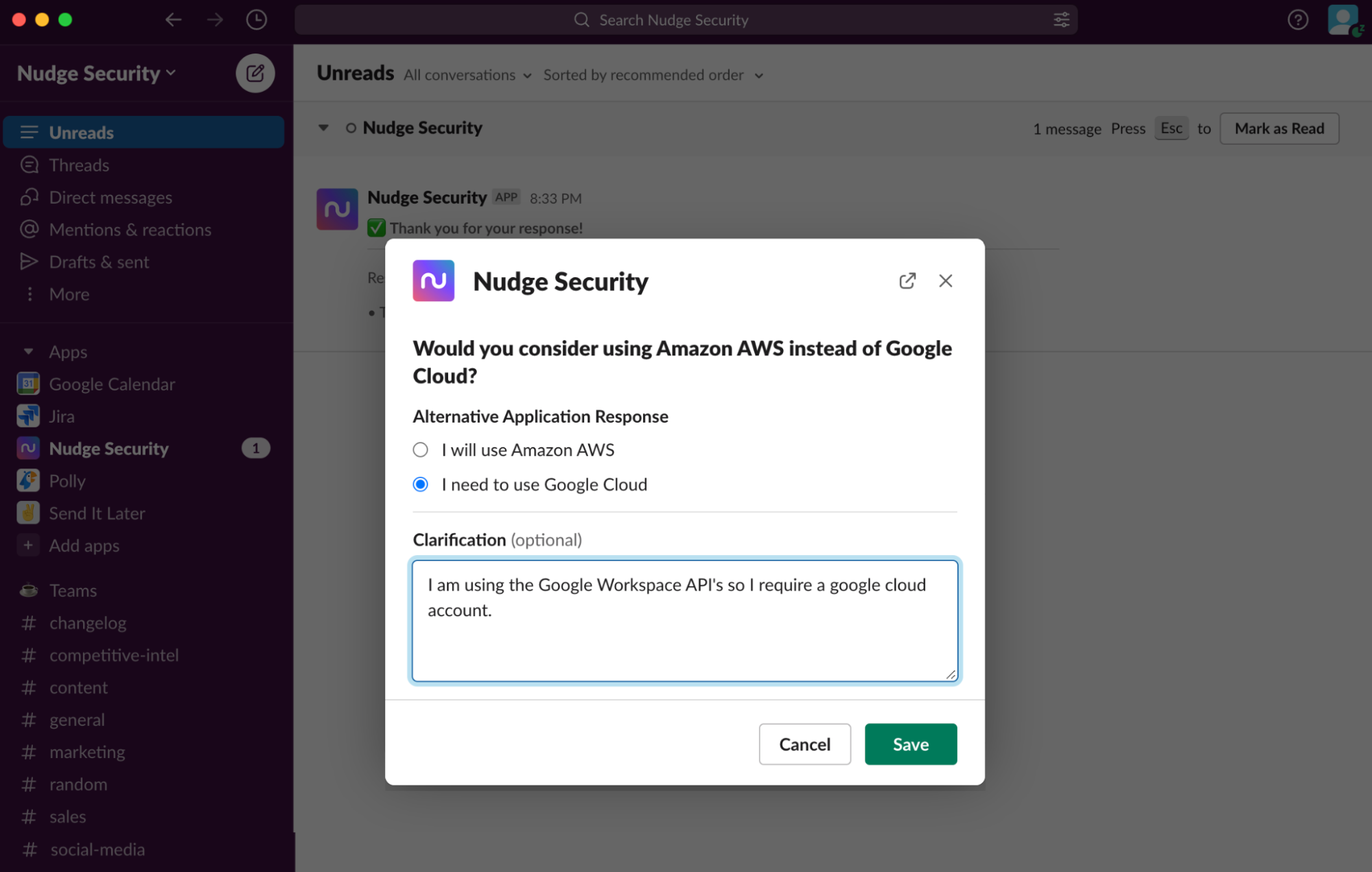
Nudge Security helps you avoid the costs and risks associated with unmanaged cloud accounts by identifying your organization’s cloud accounts and making it easy for you to move them into centralized governance.
Take Nudge Security for a test drive and discover all the SaaS and cloud assets at your organization, including rogue cloud accounts and shadow IT. Try it free for 14 days.